Azure AD Connect–Identity in the Cloud, SSO Azure AD
The idea is – hundreds (maybe thousands) of applications – but just a SINGLE Identity (that works across all the apps)s.
Three Models for Authentication
In all these models, identity between on-prem and Azure AD needs to be synchronized.
- Authenticate in Azure (Using Azure AD Connect)
- Authenticate against On-Prem AD (Windows Server AD) – by passing credentials from Azure to On-Prem using ADFS
- Seamless SSO
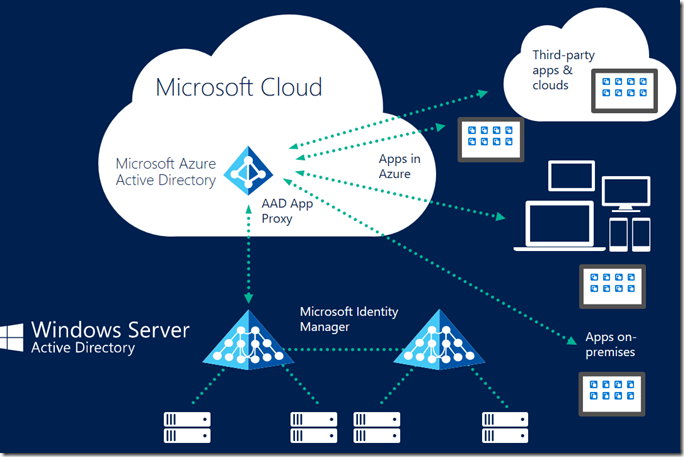
Seamless SSO
In order to avoid authenticating already authenticated users, a pass through agent is provided. Essentially, you add in two more infrastructure components – an AD Proxy (on the Azure side) and Connectors (on each of the apps).
- Azure AD app proxy is a cloud service that allows users to access on-premises apps securely.
- Users connect to the cloud service that routes traffic to the applications via connectors. Connectors are usually deployed inside the corporate network, next to the applications.
- Users connect to the cloud service that routes their traffic to application resources via the connectors.
Note: OWASP Recommendation – Store the secondary SSO / framework / custom session identifiers in native session object – as opposed to sending as additional headers or cookies.
Authenticate in Azure
Authenticate with Azure AD Connect (Service). Between Windows Server AD and Azure AD – perform Identity + Password (Hash) synchronization.
Summary
IAM in the cloud is a combination of Windows Server Active Directory, Microsoft’s Identity Manager and Microsoft’s Azure Active Directory. With the combination of an AD in Azure and an AD on-prem, there are a multitude of authentication options available for providing a single point of IAM for multiple apps.
Leave a Reply