Private Subnets and VPN Tunnels in AWS
VPN Tunnel
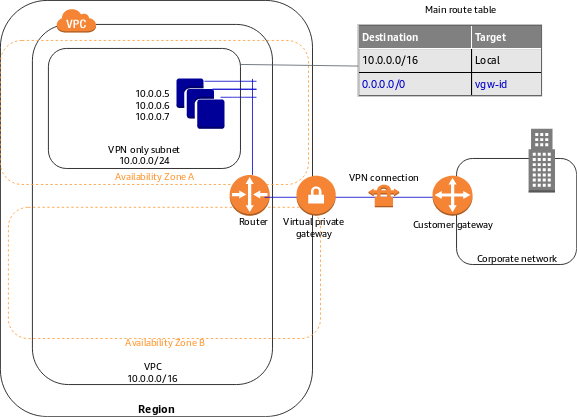
The idea is for all your private subnets to route via the VPN Tunnel. Create a custom route table shown below for the first private subnet. This is the same routing table you will attach to successive subnets. A SINGLE routing table can have multiple routes
Testing the VPN Tunnel
| Protocol type | Protocol number | ICMP type | ICMP code | Source IP |
|---|---|---|---|---|
| ICMP | 1 | 8 (Echo Request) | N/A | The public IPv4 address of your on premises computer or cidr range |
- Spin up an Ec2 instance, associate it with a SG that allows PING traffic (ICMP). Now, get its private IP address (for example,
10.0.0.4). The Amazon EC2 console displays the address as part of the instance’s details. - From a computer in your network that is behind the customer gateway device, use the
pingcommand with the instance’s private IP address. A successful response is similar to the following:ping10.0.0.4
PRIVATE Subnets need a route to both the Internet (Nat gateway) and to the VPN Tunnel (VgW). How do you provide both in one custom route table?
The ‘destination’ fields are different.
- For Private Subnets getting to On PRem Addresses – the destination is anything in the VPC (entire CIDR block – 10.0.0.0/16) and target is VgW
- For Private Subnets getting to Internet, the destination is 0.0.0.0/0 and the target is the NAT GW
Leave a Reply