AWS IAM and Monitoring
Why do you need Roles?
Instances and Apps On Instances need to access AWS services. Say an S3 bucket. Now, you can either provide access keys to accomplish this. But keys are hard to store and manage.
So – you could define a ROLE. A Role is what the Role assignee is ALLOWED to do. Say you define a ROLE for an EC2 instance. Any app that runs on that instance can assume that role. Now, if the app needs to call S3 storage – we simply attach that specific S3 policy to the ROLE.
We avoid storing keys / credentials for each application that needs AWS services.
How do you delegate cross account access?
Say you have two accounts – Production and Development. Development needs access to production.
You would define a ROLE. When creating the role, you can define the Development account as a trusted entity and attach/specify a permissions policy that allows trusted users to update the productionapp bucket.v
Q: How do you set granular permissions using policies?
Using policies, you can specify several layers of permission granularity. First, you can define specific AWS service actions you wish to allow or explicitly deny access to. Second, depending on the action, you can define specific AWS resources the actions can be performed on. Third, you can define conditions to specify when the policy is in effect (for example, if MFA is enabled or not).
How do you delegate cross account access?
Say you have two accounts – Production and Development. Development needs access to production.
You would define a ROLE. When creating the role, you can define the Development account as a trusted entity and attach/specify a permissions policy that allows trusted users to update the productionapp bucket.
Q: How do you set granular permissions using policies?
Using policies, you can specify several layers of permission granularity. First, you can define specific AWS service actions you wish to allow or explicitly deny access to. Second, depending on the action, you can define specific AWS resources the actions can be performed on. Third, you can define conditions to specify when the policy is in effect (for example, if MFA is enabled or not).
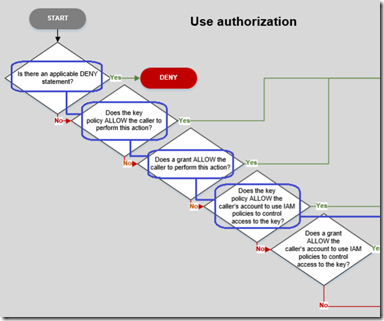
Is there a DENY policy in place?
CloudWatch
Using CloudWatch metrics, you’re also able to set CloudWatch Alarms to trigger an action in real-time from simple notification to stopping an under-utilized EC2 instance.
Integrate with CloudTrail
Using CloudTrail’s ability to log a change to a resource, a CloudWatch Event rule can be created to recognize this and then trigger a Lambda function to open a ticket for investigation.Using CloudTrail’s ability to log a change to a resource, a CloudWatch Event rule can be created to recognize this and then trigger a Lambda function to open a ticket for investigation.v
Landing Zones – Greenfield Implementation – How many accounts are created? And how much does it cost me?
Four accounts in all, including the master account.
- Master: This is where you will find the AWS organisation. Also found here are Single Sign-On (SSO) and a service catalog for the ‘Account Vending Machine’ (AVM), which automates the process of creating new AWS accounts.
- Security: Contains roles that allow you to switch to other accounts or receive notifications of security incidents.
- Shared services: Contains Active Directory and other services that are used by all accounts.
- Logging: This is the central landing place for logs, such as CloudTrail audit logs.
Leave a Reply