Firewalls versus Security Groups–AWS
Also read AWS NACLs versus Security Groups and Service Accounts as an intelligent firewall option on GCP
Security Groups are like ALLOW/DENY firewall rules – either allowing individual connections or blocking them – based entirely only on source IP addresses and ports.
A security group will not inspect content – it will let in a virus if it is coming from a trusted IP.
To inspect content, you would need an actual firewall (either a virtual firewall or a physical firewall appliance).
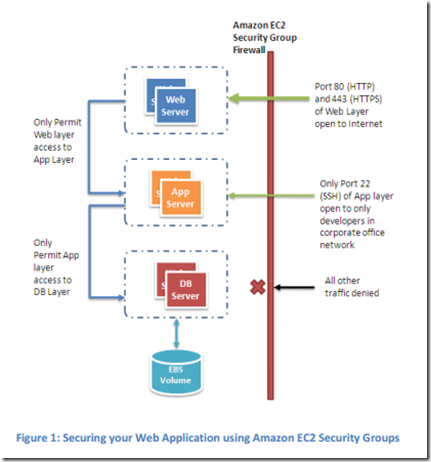
Typical AWS Security Model for a 3 tier app
Typically, AWS recommends using security groups to protect each of the three tiers. The SG can be configured to let in specific ports – and disallow specific ports (both inbound and outbound).
Web Application Firewall
AWS offers a firewall – called WAF – for your web applications. From their online documentation:
You can use AWS WAF to create custom rules that block common attack patterns, such as SQL injection or cross-site scripting, and rules that are designed for your specific application. New rules can be deployed within minutes, letting you respond quickly to changing traffic patterns. Also, AWS WAF includes a full-featured API that you can use to automate the creation, deployment, and maintenance of web security rules.
Summary
Simply creating a security group around your AWS instances will not protect you from malicious software. A security group is unable to inspect content. To truly protect your instances from malware, you will need an actual firewall – or a firewall service offering such as WAF (from AWS). WAF CAN actually check for common attack patterns such as SQL Injection and XSS.
Leave a Reply