Public Private Subnets in GCP, Subnet and Instance Routing
In AWS, one could look at the routing table to determine if an Internet Gateway was an established route (i.e. if all instances were able to route to the IgW). If this were true, then the subnet is automatically deemed a public subnet. If this is false, then the subnet is deemed a private subnet.
On GCP, there is no need to look at routing tables (the routes are automatically created as independent resources – you will still need to associate each compute instance with an internet route)
Public vs Private subnet on GCP?
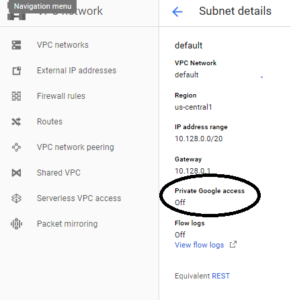
Private Google (GCP) access – enabled / disabled
This is the key to determining if a subnet is PUBLIC or PRIVATE in GCP. Click on the specific subnet and look for the value of ‘Private Google Access’ (see image below).
When you create your subnet, you are asked about this value. When this is PUBLIC (private gcp access disabled), then each instance launched in this subnet will be associated with the internet route. The image shows this internet route (it is a system generated default route).

Default Subnets in Default VPC in GCP
In GCP, a default VPC spans ALL regions. It creates a subnet in every single region of the world.
For better or worse, each of these subnets is PUBLIC (see screenshot below). Private access is disabled. As far as I can tell, there isn’t a way to modify a PRIVATE subnet to a PUBLIC subnet.
Subnet Routing and Instance Routing – Default Routes, Custom Routes and Route Order
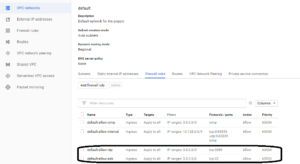
When you add a default VPC, there are a set of default routes added. Since all the subnets in a default VPC are PUBLIC, you will notice an internet route in the set of routes (go to the console menu–>Networking–>Routes)

Instance Routing
Instances in the default subnets will automatically get all the default routes associated – i.e. – you do not need to do anything special to provide an instance with a route to the internet as long as that route exists. This is the most important thing to understand about GCP Subnet Routes. What are default routes? There are only TWO categories to worry about – the default internet route and default SUBNET routes (one for each subnet).
The second most important thing is to understand the ORDER in which routes are evaluated.
Custom Routes (as opposed to Default Routes) : There are cases where you want to create custom routes for individual VMs. Custom routes are typically static routes that you add manually. There are also dynamic routes (which also fall under Custom Routes) that are automatically created by Cloud and are meant for addresses outside of your typical VPC CIDR block.
Route Ordering
For outbound traffic from a compute instance, GCP selects one route according to the following routing order :
- Subnet routes are considered first because Google Cloud requires that subnet routes have the most specific destinations matching the IP address ranges of their respective subnets. f the destination for a packet fits inside the destination of a subnet route, it is delivered to that Google Cloud subnet. You cannot override a subnet route with any other type of route.
- Subnet Route wins over Static Route – GCP does not allow you to create a custom static route that has an equal or more specific destination than any subnet route.
- Static wins over Dynamic – A static route with the same prefix and route metric as a dynamic route always has a higher priority than the dynamic route, so that any conflicting dynamic routes are ignored.
- When you connect VPC networks by using VPC Network Peering, the networks share all subnet routes. Google Cloud prioritizes subnet routes in peer networks similar to the local network’s own subnet routes: subnet routes in peer networks must have the most specific destinations.
- If the packet does not fit in the destination for a subnet route, GCP looks for a custom route with the most specific destination.
Suppose that the destination for a packet leaving a VM is 10.240.1.4, and there are two routes with different destinations: 10.240.1.0/24 and 10.240.0.0/16. Because the most specific destination for 10.240.1.4 is 10.240.1.0/24, the route whose destination is 10.240.1.0/24 defines the next hop for the packet.
Firewall rules
These rules exist at the VPC level. For a default VPC, you will see RDP and SSH access enabled.
Summary
For those coming from AWS, it isn’t immediately obvious how subnets in GCP work – and how they are designated as Public vs. Private. Also, routes for instances in the subnet are not the same as in AWS. Routes are independent entities that are automatically associated with instances. Instances do not need to do anything special to pick specific routes. Routes are evaluated in a specific order – subnet routes being the highest priority with static custom routes as the second priority.
Leave a Reply